The Agile CISO: De-risking architectures and artefacts in transformation and the software supply chain
NEW – CISO 360 Software is a unique benchmarking conference that will unite CISOs, senior cybersecurity practitioners and industry luminaries internationally to benchmark within a trusted community ambience. Part of the wider CISO 360 series by Pulse Conferences, this half day virtual conference with a difference will focus on how CISOs can best measure the inherent risk in architectures and artefacts and reduce this risk against the backdrop of accelerated digital transformation, a plethora of core technologies and extended supply chains.
Join: CISO, architects, cybersecurity practitioners and risk and technology luminaries at CISO 360 Software for a candid discussion on qualifying technologies and processes to avoid costly mistakes. Now is the perfect time to share the latest case studies on how CISOs are progressing with their transformations in 2020!
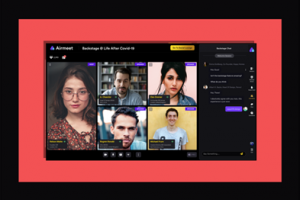
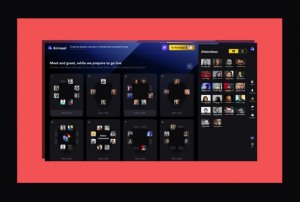
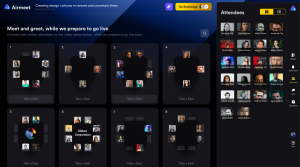
The virtual format: Take your seat at tables of 8 for in-depth comparative discussions in a smaller group networking by video style. Visibility to see where people are and easily move around to meet fellow CISOs (it is impossible to get lost!) There is a continuously chaired live interactive live broadcast with keynotes and future-facing panels interspersed with discussions and topped off with fun 3-minute random video speed networking (don’t worry you can discretely skip over people you don’t want to meet!).
Speaker in the Spotlight
Richard Hollis – Risk Crew
“Is there a better way to test the security integrity of applications that have already been deployed – but were not subject to SDLC security best practices? “
Key discussions areas
Benchmarking cybersecurity approaches to 6 risks inherent in transformation architectures and artefacts
- Cloud security
- Securing core mobility technologies
- Identity infrastructures
- Artificial Intelligence and Machine Learning
- IoT
- Big data and analytics
Discussion Focus: Managing Cybersecurity Risk in the Supply Chain and Transformation
Share practical experiences and brainstorm challenges with peers. Do we have effective ways to measure security ROI? How can we benchmark our progress? What are proven ways to communicate risk mitigation and metrics to the Board?
- Software supply chain risk
Connectivity level – How can we keep track of how others access our process and systems?
Product level – How safe is the product and how can we develop a clear risk-based approach?
How can we collectively mitigate this attack vector risk? - Transformation risk
What core technologies are game changers for security in 2021 and beyond, how and why?
How are we achieving security by design? What does ‘world class’ look like that we can aspire to?
Topics for CISO 360 Software
How can we keep track of how others access our process and systems and gain assurance? Trust or Accountability – Is there a trade off? How can we achieve continuous assurance of our supply chain? How far do we go?
How safe is the product and how can we develop a clear risk-based approach? Why do we trust some brands and not others?
Risk Metrics Café – CISO Industry benchmarking. As CISOs, where do we set the risk bar with transformation and core technologies? How can we get a view on what does your posture/risk look like (almost) right now … not what it looked like 11 months ago? What risk models are we using to plot out our maturity curve against risk curve? How are we benchmarking and articulating our own risks to the Board?
Skills and Cultures for the journey ahead – Post digital transformation resilience building.
So are you SASE? Demystifying the buzz – What SASE announcements are expected over the next year as vendors merge products and/or partner to compete in this emerging market?
How can we achieve continuous monitoring and better visibility? What is our process for monitoring activity in real time? Understanding behaviours and pros and cons of SIEM tools.
Secure Cloud: How we as CISOs can leverage business opportunities that lie within cybersecurity during transformations? From protecting Intellectual Property portfolios to securing and supporting the best customer experiences?
Software Development and the CISO. Securing the continuous integration (CI) and continuous delivery (CD) process. How can CISOs gain influence over technology projects from the outset? Securing an expanding infrastructure – adapting to the speed of product delivery
What is the relationship between the inherent risk of a digital asset and the cyber insurance value? Can cyber premiums drive good practice?
Is cybersecurity the biggest risk of digital transformation? CISO interaction with different roles. Products and Services. Big Data, AI and ML. Business and Brand. Legal and Procurement
Ways to interact at CISO 360 Software
During the event, you will be able to:
- ‘Take a seat’ at a table and talk to fellow attendees during breaks and pre event much as you would in a physical event
- Participate in live facilitated think tanks with 8 CISOs maximum on each table to benchmark in-depth on how we are maximising the value of security during transformation
- Participate in 3-minute randomly selected video speed networking – meet peers and strategists for ice-breakers!
- Share insights publicly via the chat during discussions on the main stage to stimulate the debate
- Chat privately with peers both during the Sessions and at table level in the Social Lounge
- Ask and upvote questions throughout the event where the chairperson will pull them out for the Speakers attention during Q&A!
- Join Speakers live on the stage to ask a question or share insights by video as a spotlight speaker – simply ‘Raise’ your digital hand!
- Vote yes or no. See the results when you vote
- See what’s coming up on the agenda. Our chairperson will lead the day as a continuous live broadcast interspersed with short and frequent breaks for networking and a breakout for think tank discussions